Updated on January 15, 2025

The healthcare industry generally deals with data sets that are large, with Patient Health Information (PHI) and personal data.The patients entrust the healthcare institutes to safeguard this data using the highest standards. To ensure this, the US federal government came out with HIPAA and SOC regulations.
In this blog, we explore the nuances of these federal standards. We will tell you what exactly you need to know about these regulations if you are a healthcare institute.
We will also cover:
- What is HIPAA compliance?
- Which organizations need to be HIPAA compliant?
- HIPAA rules and regulations – an overview.
- What is Email Compliance in HIPAA?
- Violation types and fines?
- SOC2 certification?
Let’s go.
What is HIPAA compliance?
HIPAA stands for Health Insurance Portability and Accountability (HIPAA). The Department of Health and Human Services (DHS) came out with these standards in 1996.
HIPAA aims to protect private patient data in both physical form and electronic form. The Office for Civil Rights (OCR) enforces HIPAA regulations. Healthcare organizations must implement HIPAA compliance chatbot to ensure that patients can trust them with their private Protected Health Information (PHI). HIPAA aims to safeguard the security and integrity of PHI.
In simple terms, what the government is trying to tell healthcare institutions is, “Do not disclose patient’s sensitive healthcare data to others, and keep it safe.”
Which organizations need to be HIPAA compliant?
If you are a healthcare organization in the US, you must comply with HIPAA rules. These organizations have then been classified into two categories. They are:
1. Covered entities:
If you are someone in the US who is directly involved in delivering healthcare services, HIPAA classifies you under Covered Entities (CEs).
These may include medical practitioners such as physicians, dentists, pharmacists, nurses and also nursing homes, hospitals and clinics. If you are an organization that provides health insurance coverage, you will also have to adhere to HIPAA regulations.
2. Business associates:
Business Associates have access to PHI, and while they do not directly provide healthcare services, they are privy to patients’ data. Generally, they perform services on behalf of Covered Entities (CEs).
Business Associates may include EHR vendors, IT service providers, billing companies responsible for processing claims, or consultants. If you deal with patient data, then you are classified as a Business Associate. This can include organizations that provide data storage or data transmission services of PHI.
Not any one of the two categories mentioned above? You still need to comply with some of the provisions of the Administrative Simplification section of HIPAA. If you are a vendor of Personal Health Records (PHRs), or a PHR-related entity, you must comply with the HIPAA Breach Notification Rule.
HIPAA Rules and Regulations – An Overview
Here is a small overview of HIPAA Rules and Regulations.
1. HIPAA Privacy Rule:
The HIPAA Privacy Rule aims to protect the privacy of patients by not giving any unauthorized access to PHI. The Privacy rule establishes national standards to protect PHI. It also places strict limits on the disclosure and use of this information.
The HIPAA Privacy Rule applies to healthcare providers, health plans and also business associates who transmit electronic PHI (ePHI). The Privacy Rule is applicable to both Covered Entities and Business Associates mentioned above. An example of this may be a third-party IT service vendor or a cloud storage provider of patient data.
2. HIPAA Security Rule
The HIPAA Security Rule is applicable specifically to Electronic Patient Health Information (ePHI). It sets guidelines and implements technical safeguards with an organization’s IT infrastructure. Organizations implement the HIPAA security rule to maintain ePHI confidentiality and prevent unauthorized access.
The HIPAA security rule consists of three major subcategories, which are:
- Physical safeguards: Physical safeguards are the steps that an organization has taken to protect the physical devices where ePHI storage happens. This can involve advanced measures such as access control, workstation security measures, etc.
- Administrative safeguards: Administrative safeguards are the policies that an organization’s management actively takes to protect ePHI. An incident response plan and workforce training programmes are examples.
- Technical safeguards: Bigger healthcare organizations use firewall and encryption tools so that there is no unauthorized access to ePHI. These come under technical safeguards. This also consists of audit controls for monitoring system activity.
3. The HIPAA Breach Notification Rule:
Data breaches are a serious threat that a lot of healthcare institutes are extremely wary of. The HIPAA Breach Notification Rule aims to mitigate the risks that organizations face when dealing with a data breach.
The HIPAA Breach notification rule requires healthcare organizations to notify patients when their unsecured PHI is used or disclosed without their permission. This data breach can be in such a way that it compromises the privacy and security of the PHI.
If you are a healthcare-covered entity and it comes to your knowledge that a breach of PHI has taken place, you have to notify the relevant parties (individuals, the Department of Human and Health Services and the media). This has to happen within 60 calendar days of the date of discovery of the breach.
If the data breach is large, and by large we mean more than 500 individuals PHI has been compromised, the covered entity must then inform a major media outlet. This media outlet must be located within the state or province in which the breach has taken place. In addition to this, the covered entity must also notify the HHS.
Email compliance in HIPAA
Should you or should you not make your email HIPAA compliant? Well that depends on how you plan to use the Electronic Protected Health Information (ePHI). If your email network exists behind a firewall, and you do not plan to exchange these emails outside of the firewall, then you need not encrypt your emails.
Think of it this way. When you are sending an unencrypted email, it is sent from your server to the recipient’s server in plain text via SMPT. This is like sending a letter with the contents written on the outside of the envelope. Any cybercriminal can access the contents of your email, like mail filters do, to see if your content is spam.
If you are, however, sending your email beyond the firewall, you need to make it HIPAA compliant. To do this, you have to implement end-to-end encryption for all your email communication like WhatsApp does for its messages. You can also use access control to ensure that only those who are supposed to receive the email continue receiving it.
Many organizations in the US that have obtained HIPAA email compliance recommend AES 128, 192 or 256 bit-encryption. If you do not have enough staff in-house to ensure that all emails that your organization is dealing with is HIPAA compliant, you can always use a third-party email service provider that is HIPAA Compliant.
Steps involved in making your emails HIPAA compliant:
Step 1: Obtain consent:
While using ePHI details for a patient or a plan member, a prior warning must be given to the recipient highlighting the risks that they must take while sending ePHI over email. You must also clearly document both the warning and the consent in case there is a discrepancy later.
Step 2: Use a HIPAA Compliant email service
As we have said earlier, you need to use end-to-end encryption on your emails if you wish to be HIPAA compliant. Make sure that if you are sending an email outside your firewall, you need to encrypt the email both at the sender’s end and at the receiver’s end.
Step 3: Ensure a Secure Email Retention System
HIPAA Rules on email retention are still a little hazy since it is not a part of HIPAA legislation. Individuals can request Accounting of Disclosures for PHI, and healthcare organizations need to maintain a database of email communications in case legal action is taken against them. HIPAA stipulates that covered entities retain documents related to their communication efforts for a minimum of 6 years.
HIPAA Violations and Fines
The Office for Civil Rights (OCR), which comes under the Department of Health and Human Services, is generally responsible for issuing fines for HIPAA violations.
Violations are pretty serious, and the fines range from $127 up to approximately $64,000, depending on the severity of the penalty.
There are 4 penalties Tiers that HIPAA has classified its violations, which are represented by the 4 squares in this quadrant.
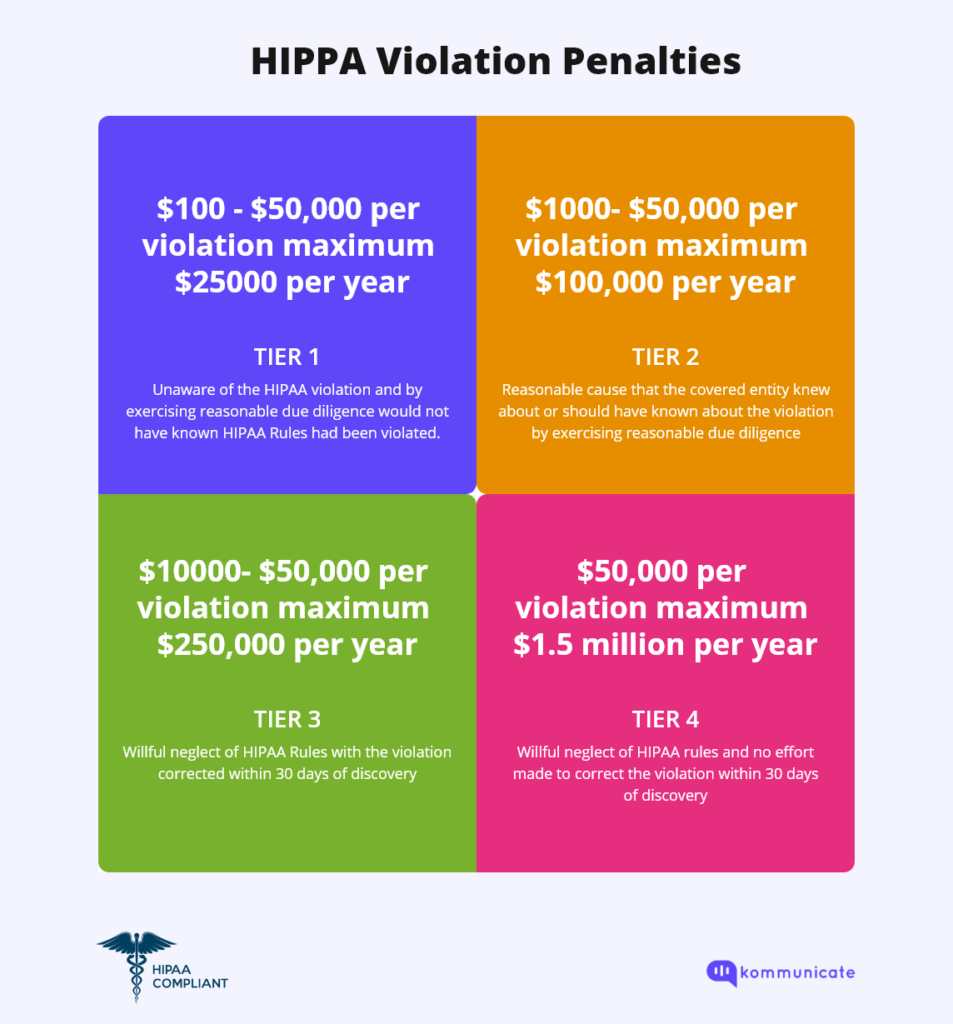
As you can see, the maximum penalty of $1.5 million per year is for healthcare organizations that knew the HIPAA rules and still willfully violated them.
HIPAA Violations generally come under 2 Categories:
Category 1: Civil penalties:
The civil penalties consist of 4 tiers of increasing culpability. There are minimum and maximum penalty amounts on each tier and also an annual cap on the penalties for multiple violations.
The four Tiers of violations include:
- Tier 1: This is when the party committing the offense was not aware of, or could not know if a HIPAA rule violation was taking place. The maximum penalty for this offense is $63,973 per violation.
- Tier 2: Tier 2 violations occur when a party knew, or should have known, that its actions were in direct violation of the HIPAA act, but it was not an act that took place due to willful neglect. The maximum penalty for this violation is $63,973.
- Tier 3: This category of violations occurs when there is a willful neglect on the part of the person or institution handling the PHI, but they have taken corrective measures under 30 days. The maximum penalty for this tier of violations is $63,973 per violation.
- Tier 4: Tier 4 violations are the most serious violations, where the concerned parties were aware that a violation of HIPAA was occurring, but there was wilful neglect on their part. The maximum penalty for this tier of valuation is $ 1,919,173 per violation.
Category 2: Criminal penalties
Criminal penalties are applicable to employers when their employees unknowingly or willingly commit violations to HIPAA rules and access PHI without authorization. The major difference between Civil and Criminal Penalties is that in the case of Criminal Penalties, it is the Department of Justice (DOJ) that has jurisdiction.
Criminal penalties can be either a big fine or even jail time, depending on the severity of the offense.
The Three tiers of Criminal penalties are:
- Tier 1: This is the lowest tier of violations, where the offender had limited knowledge that he was committing an offense. The DOJ, however, does not consider ignorance of HIPAA rules as grounds to violate it, and can impose a maximum penalty of up to $50,000, up to 1 year in prison, or both.
- Tier 2: In this tier of violations, the person who violates HIPAA has done so under false pretense. Otherwise, the person is responsible for disclosing PHI when they were legally not in a position to do so. The DOJ can impose a maximum penalty of up to $100,000, 5 years of prison time, or both.
- Tier 3: This is the most severe tier of violations, when a person willfully commits a violation of the HIPAA rules, for personal gain. The person in question here obtains PHI with the intention of selling it, transferring it or using it for commercial gain or malicious harm. The DOJ can impose a maximum penalty of $250,000, 10 years prison, or both for this tier of violation.
SOC2
SOC2 (System and Organization Control) is a set of principles with the primary aim to protect all forms of data, specifically data that technology service providers handle and store in the cloud. What this means is that every SaaS company has to adhere to SOC2 principles, if they deal with PHI.
SOC2 is based on five Trust Criteria Services. They include:
- Security: Prevention of unauthorized access.
- Availability: Ensuring that all the data, system and products are accessible.
- Processing Integrity: Ensuring that the system processing is complete, accurate and authorized.
- Privacy: Maintaining the collection, use, retention and disclosure of personal information.
- Confidentiality: Making sure that all the confidential information storage happens behind access control. This can be done through different methods such as encryption.
There are 2 Types of SOC2 reports, namely Type 1 and Type 2 reports. Type 1 is lighter, whereas Type 2 is more comprehensive.
Any SaaS company that deals with PHI on the cloud must adhere to SOC2 principles. As a healthcare institute, it is ideal in 2023 that you adhere to both HIPAA and SOC2 guidelines.
If your healthcare institution is both HIPAA and SOC2-compliant, it shows that there is a commitment on your part to protect patient data. By meeting HIPAA guidelines, you are signalling that you meet the minimum legal requirements. SOC2 acts as a reassurance that you take protection of patient data very seriously.
At Kommunicate, we envision a world-beating customer support solution to empower the new era of customer support. We would love to have you on board to have a first-hand experience of Kommunicate. You can signup here and start delighting your customers right away.